Protocol stacks are important for a variety of reasons. But what are they, exactly?
Protocol stacks are a layered collection of protocols that work together to provide communication services. Each protocol in the stack is responsible for a specific task, and by layering them, we can create a more robust and reliable system.
By the end of this article, you should have a better understanding of what a protocol stack is and the design methodology behind it.
Layered Architecture
The layered architecture pattern, often known as the “n-tier” architecture design, is a common technique for reducing complexity across numerous disciplines.
A structure is divided into parts that work together. Each part has a special job to do. The parts are arranged in layers, one on top of the other.
A simple example is the airline system:
An airplane system is a good analogy to use because computer networking is a lot like air travel: In an airplane, a passenger is being “shipped” from source to destination the same way that in a computer network a message is being shipped from one device to another.
An airline system is a complex system and its functionality, believe it or not, is organized in layers, very much like the Bluetooth LE Protocol stack or any other stack.
Think for a minute about a series of steps you take when you fly on an airline.
First, you purchase your ticket, check your bags, go to the gate, and eventually get loaded onto the plane. The plane takes off and is routed to its destination. After your plane lands, you deplane at the gate and claim your bags. If the trip was bad, you complain about the flight to the ticket agent.
Behind these actions is a structure. A layered structure.

The first layer is the customer service layer which deals with tickets. The second layer is the baggage handling layer where you check your bags at the departure airport and where your bags are unloaded and you claim them at the arrival airport.
The third layer is the gate layer which deals with loading you onto the plane and unloading you from it.
The fourth layer is the runway layer which the plane uses to take off and land.
The final layer is the air traffic control layer which makes sure that planes stay separated in the sky and that they take the correct routes.
This is a very simplified view of how an airline system works but it serves to illustrate the point that complex systems are organized in layers.
Now let’s discuss the key benefits of layered architecture.
Key features that make this design favored across multiple fields are:
- Abstraction
- Separation of concerns
- Layers of isolation
1. Abstraction
It is possible for different parts of a system to have zero knowledge about one another at the implementation level, but still, be able to interact with each other.
Based on this, abstraction is the idea of hiding the implementation details of a layer and only sharing functionality with the layer it has to interface with.
It is the separation of what a layer does from how it does it.
By keeping the details of how a layer works hidden, other layers can easily interact with it. They only need to know what that layer does and they can interface with it when they need that specific functionality. They do not need to worry about how the task is performed.
2. Separation of concerns
It is the idea that each layer should only be responsible for one thing and should not contain rules that deal with other things.
Separation of concerns makes an application simpler by breaking it down into smaller, more manageable parts. Each part does one thing, and they work together to create a whole.
It abides by the divide-and-conquer strategy which is a very effective way to reduce complexity.
3. Layers of Isolation
It is the idea that each layer should be an island unto itself, receiving input and sending output as required. It shouldn’t be influenced by anything happening outside of itself. Each layer should be self-contained.
Individual layers cannot see beyond the immediate layer with which they are interacting, and have no knowledge or care about what happens beyond.
Isolation is a good thing as it allows changes made in one layer of the architecture to generally not impact or affect components in other layers. It also makes it easier to test and debug an application because each layer can be tested independently.
The above features: Abstraction, Separation of concerns, and Layers of isolation are what make the layered architecture appealing for Protocol stacks
A Protocol Stack
A protocol stack or protocol suite is the architecture of a protocol that follows the layered architecture design principle.
The functionality of the whole protocol is broken down into component protocols that are separately managed and can be treated and designed mostly independently from one another.
A protocol stack typically contains a set of protocols where each protocol in the stack performs a specific task and is responsible for a well-defined function.
The protocols are often referred to as layers with each layer providing services to the layer above it and receiving services from the layer below it.
A typical protocol stack will be structured in an n-tier architecture pattern like this:

As shown in the image above (Protocol Stack Architecture), a protocol stack is created by dividing a protocol into n-multiple layers. In each layer, two entities communicate with each other using the appropriate protocol for that layer. They do this by exchanging data units through a channel that connects them.
Each of the protocols fulfills a portion of the overall Protocol’s functionality.
Peer-to-Peer Protocol
Protocols in a protocol stack are said to be peer-to-peer protocols.
This means that the protocol operates between two entities that are peers, at each layer.
For example, a protocol entity in the nth layer can only exchange data units with its peer entity at the same level, according to the protocol of that layer.
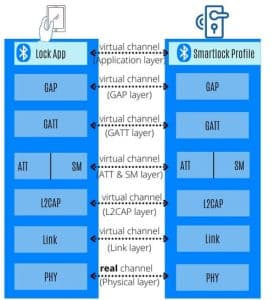
Virtual Channels + 1 Real channel
As can be seen in the image below (Application Data Transfer through a Protocol Stack), the protocol entities in the lowest level communicate with each other using a real channel. This channel is also called a physical channel. The channels of the higher layers are virtual channels.
Since the higher layer’s channels are virtual, their messages (PDUs) must be transferred from a higher layer to the one beneath it until the PDUs reach the physical layer. The physical layer will then be able to transmit the messages through the real/physical channel.
User Data Transfer Through A Protocol Stack

The highest layer in the protocol stack is called the application layer because it interacts with the user, while the lowest layer is called the physical layer because it has a real channel as opposed to virtual channels used by higher layers.
The journey of the user data from device A to device B begins as follows:
1. The user of device A(also called an initiator) uses the application on that device to ask the n-th layer protocol entity to transfer data to the application at the recipient side.
2. The n-th layer protocol entity adds its control information (PCI) to the data and passes the n-PDU message to the next layer down.
3. The (n-1)th layer entity executes a similar action…
4. Data that were generated by the application at the initiator side are thus passed down from one layer to the next lower layer, while each layer adds its own control information to the data.
5. When the data and control information added by all the layers reach the physical layer, it is all transferred through the physical channel to the recipient side.
6. On the recipient side, data flows up from one layer to the next higher layer. The protocol entity in each layer analyzes control information that was generated by its peer at the transmitting side. If everything goes well, the protocol entity passes user data it sees to the entity in the next higher layer.
7. This process is repeated until the data originally sent by the initiating application arrives at the application on the recipient side.
Let’s Recap!
In this article, we learned about:
1. The key features of a layered architecture
2. The definition of a Protocol Stack
3. Why protocols in a protocol stack are said to be peer-to-peer protocols.
4. The protocol stack has virtual channels + 1 real channel
5. How data is transferred through a protocol stack from the initiating application to the recipient one.







